asleap a Cisco LEAP and MS-CHAPv2 password cracker
As detailed on the project homepage:
Asleap demonstrates a serious deficiency in proprietary Cisco LEAP networks. Since LEAP uses a variant of MS-CHAPv2 for the authentication exchange, it is susceptible to accelerated offline dictionary attacks. Asleap can also attack the Point-to-Point Tunneling Protocol (PPTP), and any MS-CHAPv2 exchange where you can specify the challenge and response values on the command line.
Project Home Page: https://www.willhackforsushi.com/?page_id=41
Github: https://github.com/joswr1ght/asleap
Sadly, as of July 2023 – unless you’re using a legacy version of Linux / the GNU C library (glibc) asleap seems to be broken.
We’ve conducted a bit of testing and whilst asleap works on a legacy BackTrack 5 instance, it fails if built from source on a current Linux distro. The Kali package also seems to be broken.
The output below details the results of our testing.
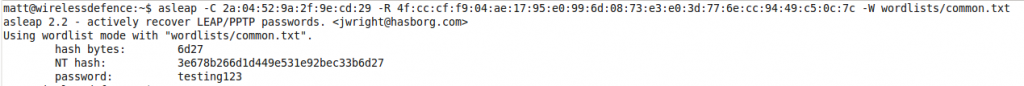
asleap v2.2 (Legacy BackTrack 5) – Works!
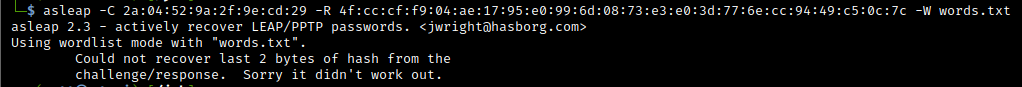
asleap v2.3 (Kali) – Broken!
zackw does have an outstanding pull request (see GitHub link above). Whilst this fixes some source compilation errors, it doesn’t appear to fix issues with asleap core functionality:
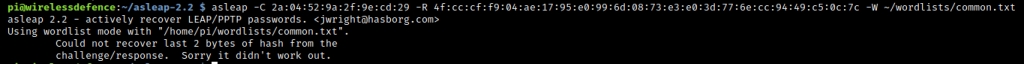
asleap v2.2 (source built – with zackw‘s “fixes”) – Broken!
Update: August 2023
A docker version of asleap has come to our attention which fixes the build issues detailed above. The image is provided by finchsec:
https://hub.docker.com/r/finchsec/asleap/tags
We can pull the image in from docker hub using the following command:
docker pull finchsec/asleap:staticNext we confirm the docker image is present (Note the image ID):
docker images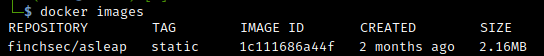
Then run asleap (Note: We have to use a slightly awkward command syntax due to the containerised nature of the docker image):
cat /pentest/wordlists/pw_topten.txt | sudo docker run -i 1c111686a44f /usr/bin/asleap -C 2a:04:52:9a:2f:9e:cd:29 -R 4f:cc:cf:f9:04:ae:17:95:e0:99:6d:08:73:e3:e0:3d:77:6e:cc:94:49:c5:0c:7c -W -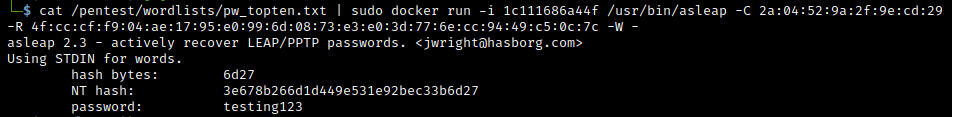
Our Opinion: Whilst the docker image provides a reasonable, if somewhat clunky workaround to get asleap working. Until asleap receives a major update you’re probably better off with hashcat (see below) or John the Ripper (JtR).
The output below was produced using hostapd-wpe. As can be seen the challenge response typically used for cracking with asleap is displayed along with JtR and hashcat NETNTLM hashes:
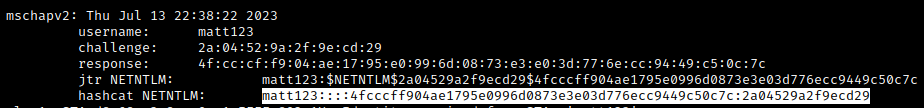
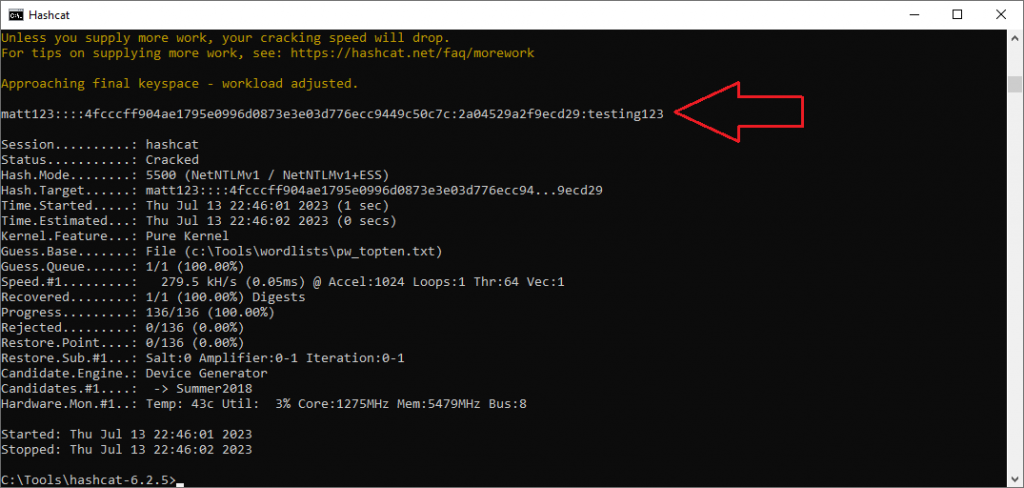
Hashcat can be leveraged using syntax similar to the following:
hashcat -m 5500 matt123::::4fcccff904ae1795e0996d0873e3e03d776ecc9449c50c7c:2a04529a2f9ecd29 c:\tools\wordslists\pw_topten.txt