Kismet Wireless Discovery Tool Overview
As detailed on the project homepage: https://www.kismetwireless.net/
Kismet is an open source sniffer, WIDS, wardriver, and packet capture tool for Wi-Fi, Bluetooth, BTLE, wireless thermometers, airplanes, power meters, Zigbee, and more.
Kismet runs on Linux, macOS, and Windows via Windows Subsystem for Linux (WSL).
Kismet can operate both headless as a standalone capture and WIDS system, or with a full modern web-based UI.

Installation
There is a comprehensive installation guide on the project homepage:
https://www.kismetwireless.net/docs/readme/installing/linux/
If you’re utilising Kali’s packaged version you just need to install it:
sudo apt install kismetWarning: We had issues attempting to install kismet from source on a Raspberry Pi 3 (1GB of RAM). The build fails at the make stage and it appears that either a lack of memory resources and/or memory access speed are the cause. Everything works fine on a Raspberry Pi 4 (4GB of RAM), albeit the build process does take a while!
Once installed (even on Kali) you’ll need to add your user to the kismet group as kismet typically runs suid-root i.e. kistmet runs as root. Configuring kismet suid-root negates the need to make use of sudo when kismet is called.
Add yourself to the kismet group (vi /etc/group) and add your user e.g.:
kismet:x:115:[your_username]You’ll now need to log out and log back in again for this to take affect.
Once you’re rebooted confirm your user is now a member of the kismet group by running:
groupsNext add your capture interface to /etc/kismet/kismet.conf e.g.:
source=wlan0Running Kismet
If all is well kismet can be started with:
kismet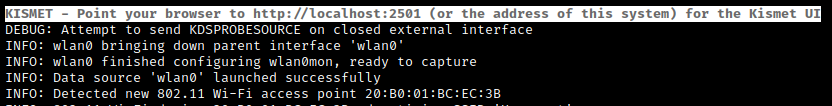
You can now point a browser to the following URL to view kismet’s device discovery portal:
http://127.0.0.1:2501/We’re actually running kismet on a Raspberry Pi, as this is headless we need to tunnel the HTTP / web connection over SSH using the following command:
Note: This ssh command isnt required if you’re running kismet locally e.g. on Kali Linux.
ssh -L 2501:localhost:2501 matt@192.168.1.12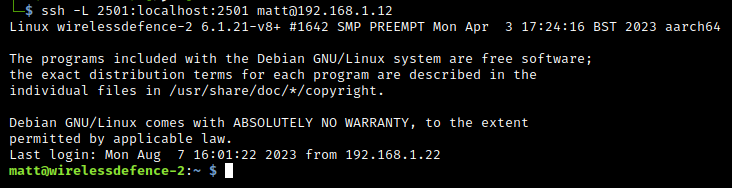
We can now access kistmet via the following URL: http://localhost:2501 or http://127.0.0.1:2501 (effectively the same URL).
On your initial connection to the webpage you’ll need to create a kismet portal username and password.
Once new credentials are created and we login, we are then presented with the main kismet display:
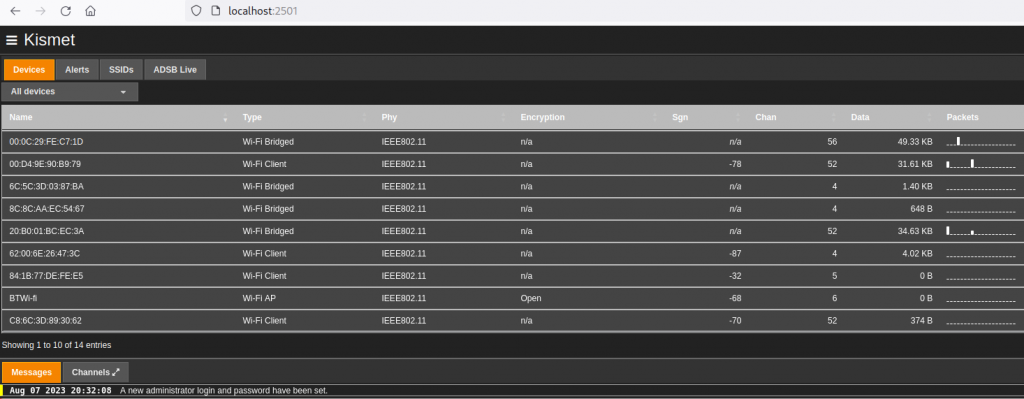
Further graphs and charts become available by drilling down into different devices / SSIDs:
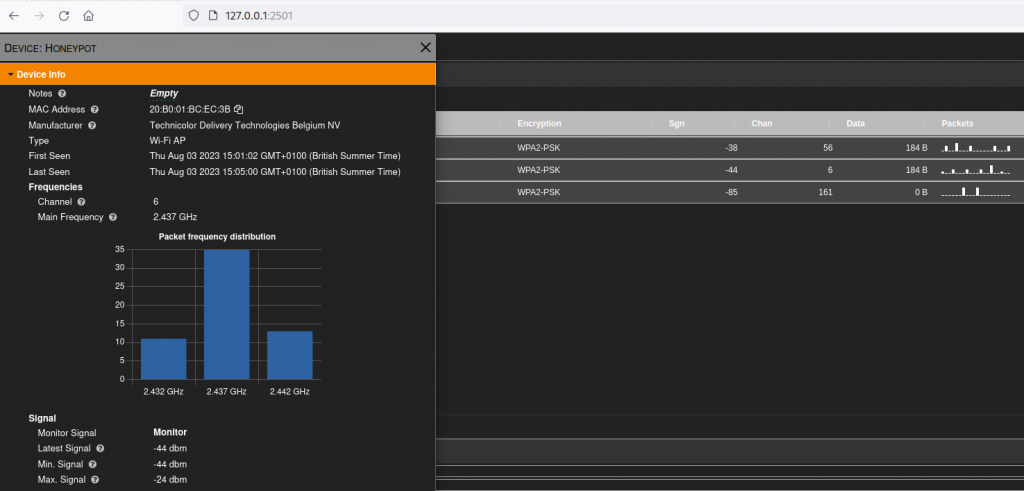
Our Opinion: kismet seems to have been around forever, and it just gets better with age. Its great for short or long term 802.11 monitoring scenarios and is a tool you should always have available in your wireless toolset.
