Creating Multiple Fake Access Points with MDK4
Note: The only prerequisite for this task is that you must use a card capable of running in monitor mode. In our case we’re using a TP-LINK TL-WN722N wireless USB adapter (see https://wirelessdefence.co.uk/usb-wireless-adapters-for-wireless-wi-fi-hacking/ for a selection of cards that support monitor mode).
To create our fake access points we are going to leverage a tool from the same GitHub as Aircrack-ng, albeit the tool has its own repo: https://github.com/aircrack-ng/mdk4
Full installation instructions are included on the repo above, or you can simply install via apt on both Kali and Raspberry Pi:
sudo apt install mdk4Now that we have our primary tool installed (mdk4) we need to create a fake Access Point (AP) list. We’ve created a list of 12 SSID / AP names in our list below, but you can have as many APs in your list as you like:
In the image below we are simply showing the status of the wireless card we are using (wlan0), for reference:

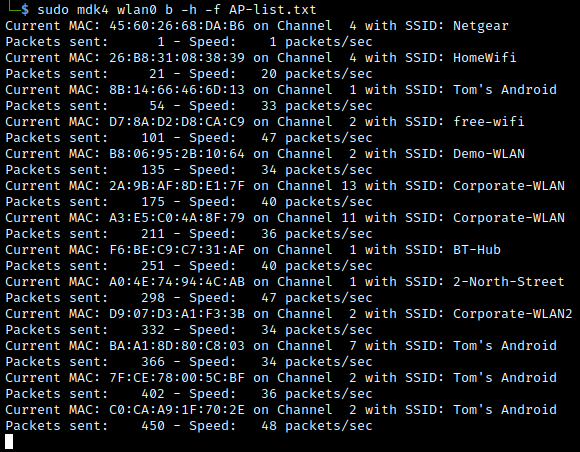
Next we simply run the following command to start sending out our spoof AP beacon frames:
The figure below details the Windows Vistumbler tool being used to perform multi-channel wireless AP discovery. As can be seen the same SSIDs from our initial list are replicated in spoofed APs identified by the scanner.
MDK4 has also created APs with randomised MAC addresses, on various channels and set different encryption and network types:
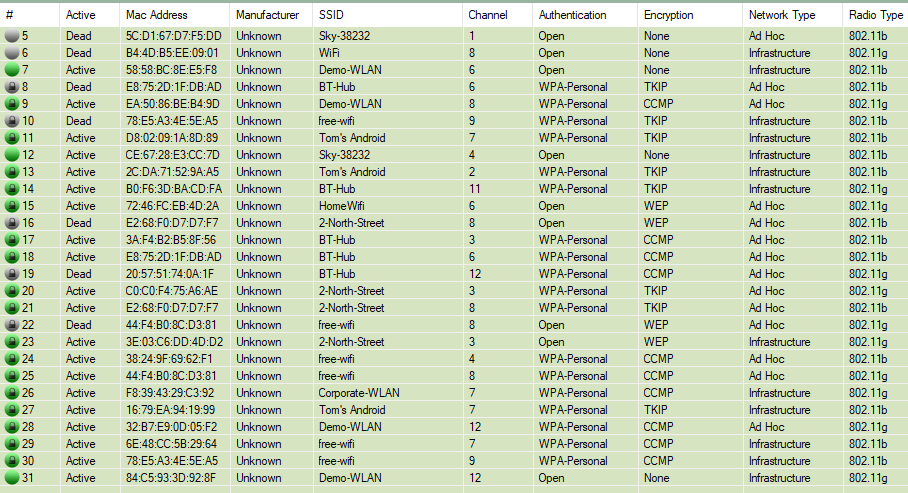
Our Opinion: Leveraging MDK4 in this way is really just a fun proof-of-concept. Aside from potentially confusing local WLAN users it doesn’t serve any meaningful purpose.
The MDK4 tool on the other hand does perform a plethora of other different tasks (post to follow).
