Discover Hidden Wireless Network SSID (without any clients)
If a WLAN is not configured to broadcast its SSID i.e. it has a hidden SSID the typical way to discover the SSID would be to use one of the following methods to capture the network’s SSID:
- Wait for a wireless client to authenticate to the target WLAN
- Deauthenticate an connected wireless client to force it to reauthenticate
Traditional SSID Enumeration (Wireless Client Required)
Whilst out-of-the-scope of this post, a wireless client can be deauthenticated and forced to reauthenticate using the following aireplay-ng command to capture the network SSID:
sudo aireplay-ng --deauth 1 -a [bssid/AP mac] -c [destination/client mac] [interface]
e.g.
sudo aireplay-ng --deauth 1 -a 00:18:39:F7:33:73 -c D8:68:C3:8A:E0:E1 wlan0Bruteforce SSID Guessing (No wireless clients required)
However, in our scenario we have no wireless clients. Thus, we need to perform SSID bruteforcing.
We can achieve SSID bruteforcing using the tool mdk4. mdk4 is a proof-of-concept tool to exploit common IEEE 802.11 protocol weaknesses
mdk4 is available from the following link: https://github.com/aircrack-ng/mdk4
In can be installed in Kali Linux / Raspbian using apt:
sudo apt install mdk4Once installed mdk4 can be leveraged as follows:
sudo mdk4 [interface] p -t [bssid/AP mac] -f [wordlist]
e.g.
sudo mdk4 wlan1mon p -t 00:18:39:F7:33:73 -f rockyou.txtIn our case once initiated SSID bruteforcing was able to acheive bruteforce attempts in the region of approximately 2000 guesses per second, although speeds as low as 1000/per second and as high as 6000/per second were also observed.
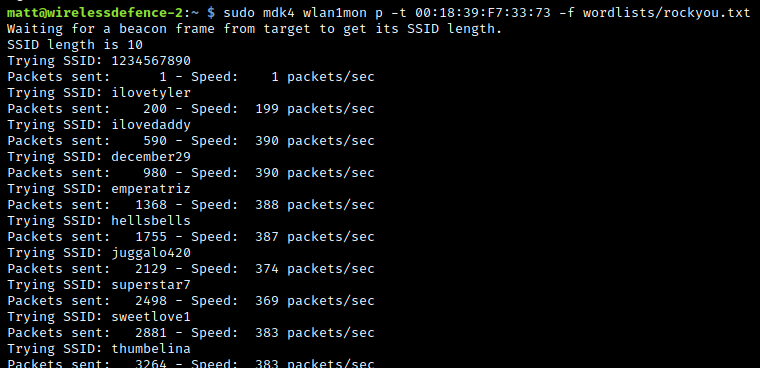
To give some idea of how long SSID bruteforcing takes; utilising the lengthy rockyou.txt wordlist which is comprised on 14,344,391 words, our bruteforce attempt (using a word towards the end of the list) took approximatley: 1 hour, 27 minutes to identify the SSID in use:
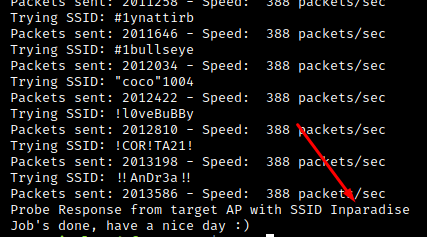
The following figure details the configuration of the target Access Point, confirming we have accurately recovered the WLAN SSID:
Useful SSID Guessing Wordlists
rockyou.txt is installed by default in Kali Linux:
/usr/share/wordlists/rockyou.txt.gzrockyou.txt can also be downloaded from:
https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
rockyou2021 is an enhanced version of the rockyou.txt wordlist is available here:
https://github.com/ohmybahgosh/RockYou2021.txt
Additionally we’ve made available a wordlist of the Worldwide top 181,542 Wireless Network SSIDs thanks to the fine work of the community and https://wigle.net/

The Worldwide top 181,542 Wireless Network SSIDs wordlist (top-wigle.net-ssids.txt) can be download from the link below:
https://github.com/wirelessdefence/wireless-wordlists/tree/main
