The single most important factor in being able to perform wireless sniffing in Windows is having a Wireless card that supports monitor mode. We have a few go to wireless cards that we typically turn to: Our Wireless Cards (article to follow).
For a more generic guide as to whether your card supports monitor mode and/or which cards to purchase , check out Aircrack-ng’s great articles:
Determine the chipset and driver of a wireless card
Tutorial: Is My Wireless Card Compatible?
Assuming we do have a compatible wireless card. Before we get started sniffing packets we are going to need two prerequisite tools.
Download both from their respective sites below:
Npcap: https://npcap.com/
Wireshark: https://www.wireshark.org/
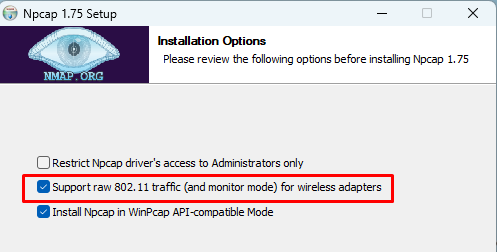
Whilst Wireshark can be installed with its default options, it is important to note that Npcap must be installed with raw 802.11 support enabled – a non-default option (see below):
The next piece of info we need is the name of our Wireless LAN adapter. This is quickly identified by right clicking on the Windows Icon > Run > “ncpa.cpl” (or similar)
As can be seen below, in our case the Wireless adapters are named Wifi & Wifi 2:

Now we have Npcap installed we have access to the command line utility WlanHelper (see references below for more info).
Now a open command shell via cmd.exe (be sure to initiate it with “Run as administrator”)
Next we query the current mode of adapter 1 “Wifi” and attempt to put the adapter in monitor mode, or Network Monitor Mode (NetMon) in Window’s terminology:
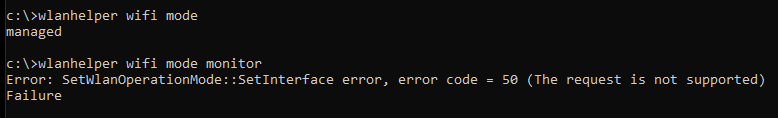
In this scenario we can see that monitor is not supported on adapter 1 “request is not supported…Failure”.
Lets try adapter 2:
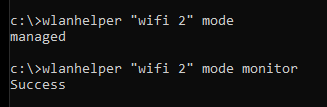
Success! We have now put wireless adapter 2 into monitor mode.
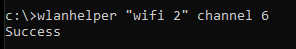
Wireless packet capture works best if the card is set to a single channel, as opposed to hopping around multiple channels. So let’s set our new monitor mode adapter to channel 6 (where we know there is an active Wireless LAN):
We’re now ready to leverage the power of Wireshark. Let’s open Wireshark and quickly confirm we have monitor mode available via the “Capture options” menu item (highlighted below):
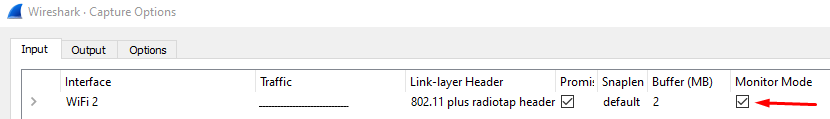
As we can see in the Capture Options below we are now in Monitor Mode:
After selecting/highlighting the appropriate adapter (Wifi 2, in our case) hit Start and you should see packets dropping in:
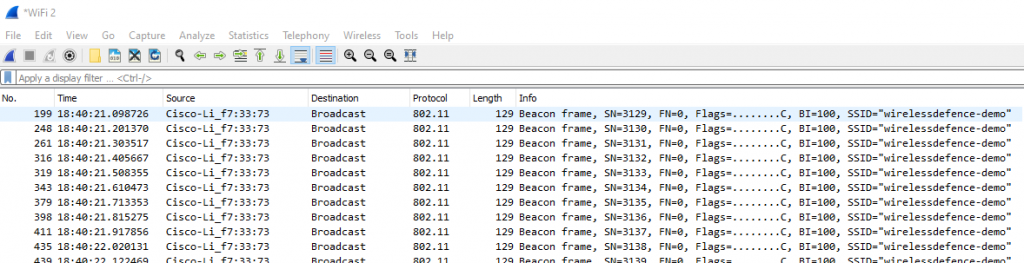
Success we are now capturing Wireless network packets in Windows.
In a later post we’ll discuss some useful Wireless LAN filters to make use of in Wireshark.
References:
