WPA, WPA2 & WPA3. What are they and what are their differences?
WPA3
Wi-Fi Protected Access 3 (WPA3) is the latest and greatest iteration of WPA so far. It offers wholesale enhancements over both WPA and WPA2, some of the enhancements and new features include:
- Replacing the Pre-Shared Key (PSK) used by WPA and WPA2 with Simultaneous Authentication of Equals (SAE), aka the Dragonfly handshake, which signals an end to offline passphrase bruteforcing
- Utilises Forward secrecy. Thus even if an attacker were to gain access to a network passphrase, they would only be able to decrypt data from that time forward i.e. they would not be able to decrypt legacy data
- The requirement to make use of Protected Management Frames (PMF) as detailed in the 802.11w wireless standard
- WPA3-Enterprise with 192-bit mode, an optional mode using 192-bit minimum-strength security protocols and cryptographic tools to better protect sensitive data
- Finally, legacy protocol use is disallowed by the WPA3 standard
Reference: WPA3 – Wi-Fi Alliance
WPA3 Security Flaws
WPA3 is not without its own issues, for example a 2019 Black Hat presentation detailed that WPA3’s Simultaneous Authentication of Equals (SAE) or Dragonfly handshake is vulnerable to side-channel attacks which could allow for password recovery attacks (via timing abuse and caching issues), WPA2 downgrade attacks and Denial of Service (DoS) attacks.
Reference: Black Hat: Dragonblood: Attacking the Dragonfly Handshake of WPA3
WPA2
The finalised 802.11i standard is implemented within Wi-Fi Protected Access 2 (WPA2) which enhances the original WPA standard by mandating the use of the Advanced Encryption Standard (AES) / Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCMP), in preference to the Temporal Key Integrity Protocol (TKIP). Albeit the enhancement in cryptographic protocol likely required a hardware upgrade in relation to wireless equipment as opposed to a simple firmware upgrade as had been possible in the migration from WEP to WPA (TKIP).
WPA
Once Wired Equivalent Privacy (WEP) had been confirmed as being broken, a timely replacement was needed to secure wireless networks. Whilst 802.11i, an enhanced wireless security standard was still a year away, elements were taken from the standard to provide an interim solution: Wi-Fi Protected Access (WPA). The beauty with the adoption of WPA was that it could be configured on the same hardware that had been used for WEP.
WPA enhanced security by introducing a cryptographic Message Integrity Check (MIC) to identify packet tampering, as well as making use of the Temporal Key Integrity Protocol (TKIP) which provided a new per packet cryptographic key.
WPA and WPA2 Security Flaws
Attacks against WPA-Personal and WPA2-Personal secured wireless networks typically involve capturing a 4-way handshake from the network. These handshakes which consist of 4 x Extensible Authentication Protocol (EAP) over LAN (EAPoL Protocol) packets can be collected whenever a wireless client successfully authenticates to a network.
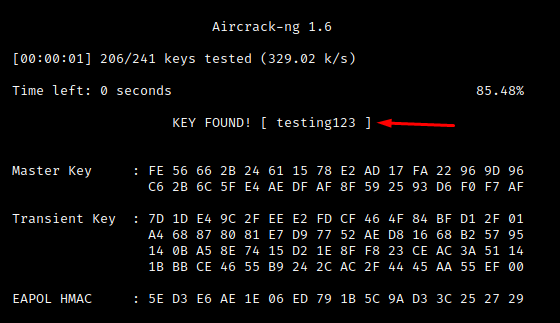
A full walkthrough of this type of attack being conducted against a WPA2 network is available here.
The figure below details a WPA2 handshake being cracked to recover the networks Pre-Shared Key (PSK):
No discussion of Wireless security would be complete without mentioning Wired Equivalent Privacy (WEP).
See the following article for more details: WEP – An Overview
